Ansible is a powerful IT automation tool that can be used to manage and configure systems across a wide range of platforms. It is a popular choice for businesses of all sizes, as it is easy to use and can be scaled to meet the needs of any organization.
One of the key advantages of Ansible is to be a multi-platform tool. This means that it can be used to manage systems running Windows, macOS, or Linux. This makes it a versatile tool that can be used to handle a wide range of devices and applications.
Ansible is quite versatile; it can be used to install, configure, and manage any type of system. Here are some examples of tasks it can do:
- Install and configure software
- Update operating systems
- Manage network settings
- Configure security policies
- Deploy applications
- Improve the efficiency and effectiveness of IT operations
Examples of Ansible Usage
Here is an example of how Ansible can be used to improve the security in a bunch of machines in the blink of an eye.
First, the installation is easy.
In Ubuntu 22.04:
$ sudo apt install ansibleFor Red Hat-based systems (like CentOS, Fedora), you can use:
$ sudo yum install ansibleOnce Ansible is installed, you can create a playbook to automate the installation of ClamAV and UFW firewall. A playbook is a collection of Ansible tasks that are executed in a specific order.
The following is an example of a playbook that installs ClamAV and UFW firewall.
The code tree is as follows:
├── clamav-installation.yml
├── main.yml
└── roles
└── clamav
├── tasks
│ ├── clamav-installation.yml
│ └── main.yml
└── templatesHere are some of the benefits for using this structure:
- Roles allow you to separate configuration code from infrastructure code. This makes it easier to understand and maintain the code, as each type of code is in its own folder.
- Roles allow related tasks to be grouped together. This makes it easier to organise code and execute related tasks together.
- Roles make it easy to reuse code. This can save developers a lot of time and effort.
- templates have the files you can use to move this data to the host.
And let’s now get our hands dirty with the playbooks implementation.
main.yml

Its structure is the same than the previous one, but it’s is an interesting option to separate new tasks in yml files when we need to separate tasks execution.
roles/clamav/tasks/main.yml
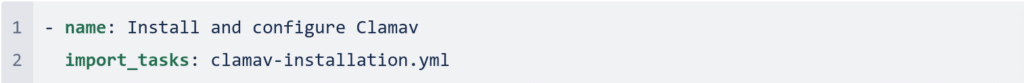
Define the playbook or playbooks to be run on this task.
roles/clamav/tasks/clamav-installation.yml
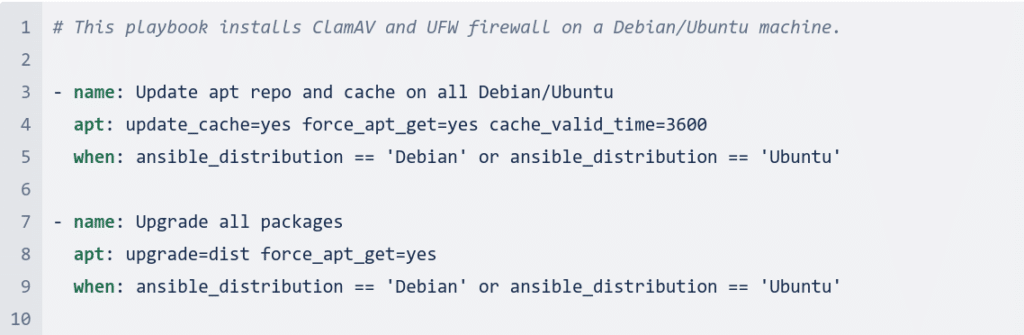
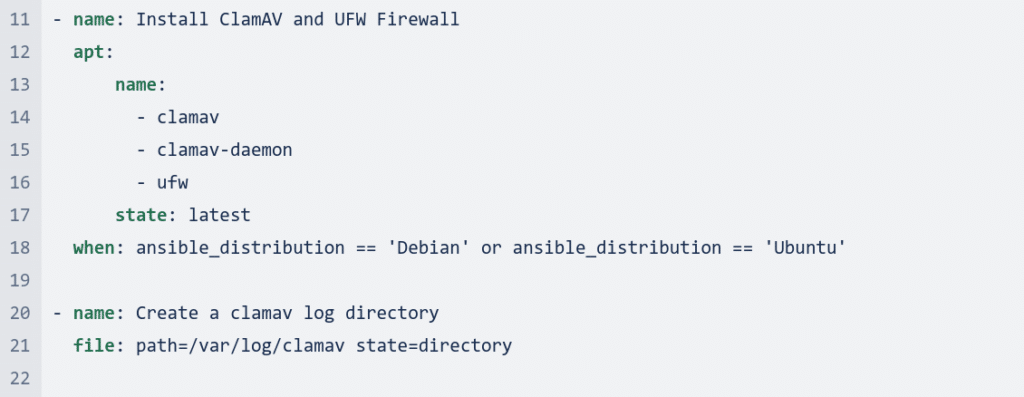


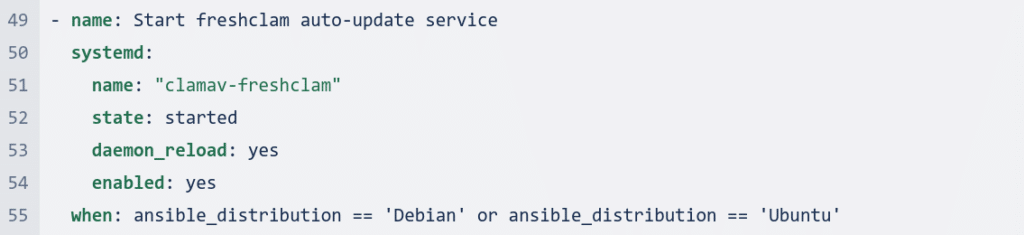
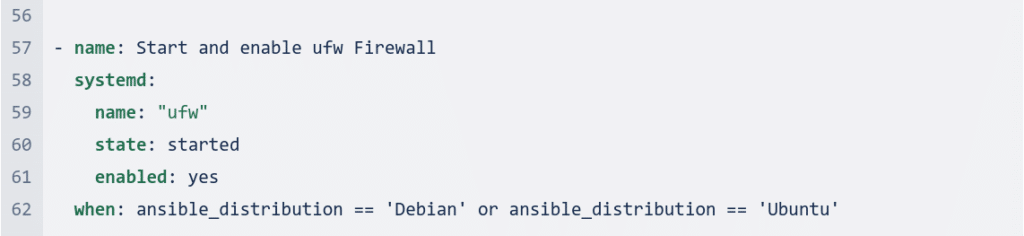
The code first updates the apt repository and cache on all Debian/Ubuntu machines. It then upgrades all packages. Next, it installs ClamAV and UFW firewall.
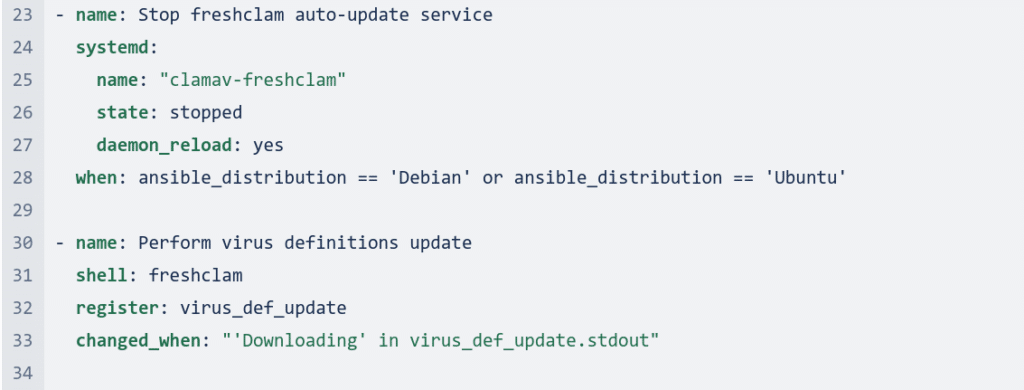
It then creates a clamav log directory. After that, it stops the freshclam auto-update service.
It performs a virus definitions update. Next, it allows outgoing connections and denies incoming connections.
Finally, it restarts the freshclam service and starts the UFW firewall.
Here is a more detailed explanation of each task:
update_apt_repo: This task updates the apt repository and cache.upgrade_packages: This task upgrades all packages.install_clamav_ufw: This task installs ClamAV and UFW firewall.create_clamav_log_directory: This task creates a clamav log directory.stop_freshclam: This task stops the freshclam auto-update service.perform_virus_definitions_update: This task performs a virus definitions update.allow_outgoing_connections: This task allows outgoing connections.deny_incoming_connections: This task denies incoming connections.restart_freshclam: This task restarts the freshclam service.start_ufw_firewall: This task starts the ufw firewall.
The when statement is used to control where the code is executed. In this case, the code is only run on Debian/Ubuntu machines.
Conclusion
We have seen how to improve the security in thousands of machines with just one command (ansible playbook).
But this is just one of the advantages you can take from Ansible. Keep in mind that you can also update your OS or easily automate the deployment of apps.
Now it’s your turn! What do you want to improve in your machines? Maybe you need to install a security critical package update? Do you need to adjust some network settings in one hit? Just give it a try and check it out.
Special thanks to Álvaro Garrido from the Novatec’s SRE team for reviewing this article.